AWS Series — Best Secured Ways of Networking
We know that Virtual Private Cloud offers good amount of protection to our resources within it. You open up the internet for the VPC using Internet Gateway which basically have your resources publicly accessible or you can use VPC peering which opens up the VPC to other VPC resources to access as if it was in same VPC.
To open our application up to other VPCs we either:
- Open the VPC up to the internet
This comes with different security considerations so everything in the public subnet is going to be public and we have lot more to manage like Internet Gateway, Network ACLs, Security Groups etc.,
- Use VPC Peering
You will have to create and manage many different peering relationships especially if you think about scaling the resources. Also, the whole network will be accessible via VPC peering if you explicitly allow all traffic within security groups and NACLs from the peered VPC. This isn’t good if you have multiple applications within your VPC.
What is the best way to expose service VPC to other tens of VPCs?
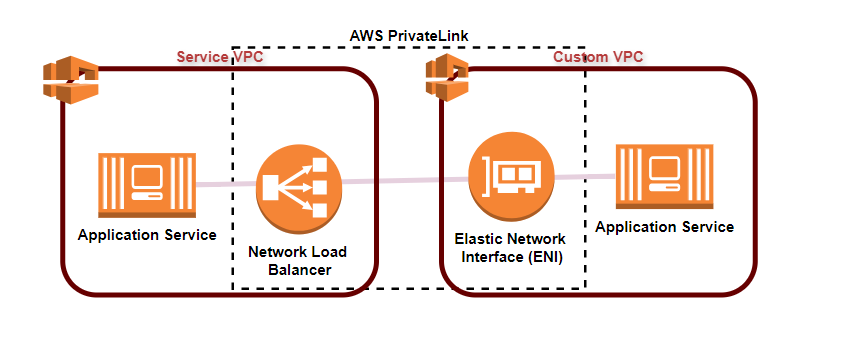
- The best way to expose a service VPC to tens, hundreds or thousands of custom VPCs by using AWS PrivateLink.
- Doesn’t require VPC peering, no route tables, NAT gateways, internet gateways, etc.,
- Requires a Network Load Balancer on the service VPC and an ENI on the custom VPC.
This is kind of like VPC peering except you are doing it at scale and not actually creating a peering relationship using PrivateLink.
It is the way to open up your VPC to hundreds and thousands of VPCs.
What if we have multiple sites which has its own VPC connection?
If you have multiple sites, each with its own VPN connection, you can use AWS VPN cloudHub to connect those sites together.
- It works on Hub-and-spoke model
- Low cost and easy to manage.
- It operates over the public internet, but all traffic between the customer gateway and AWS VPN CloudHub is encrypted.
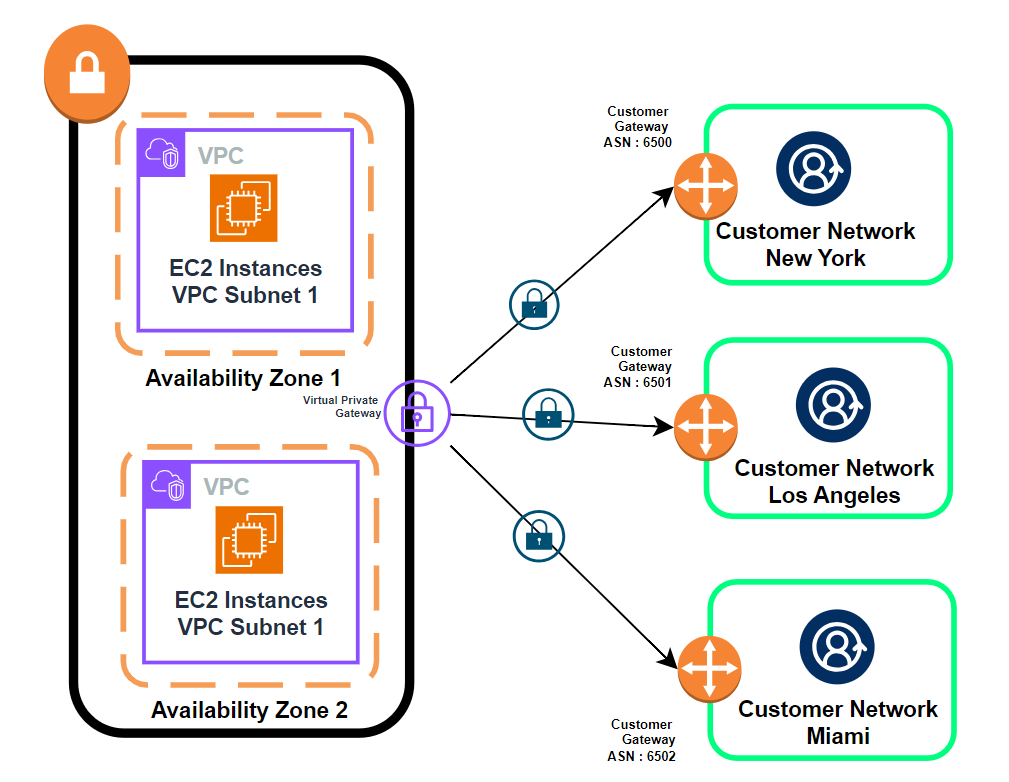
Let’s say we have got 2 VPC and we have 2 different subnets in 2 different Availability Zones. We have got a Virtual Private Gateway for our VPN connections. Let’s say we have 3 customers who has offices in New York, Los Angeles and Miami. If they use the VPN CloudHub, it aggregates the VPN connections. So the customers in New York can use that VPN connection to talk directly to Miami customers using VPN CloudHub.
With AWS VPN CloudHub, If you have multiple sites, each with its own VPN connection, you can use AWS VPN CloudHub to connect those sites together.
AWS VPN CloudHub is a low cost and easy to manage. Though it operates over the public internet, all traffic between the customer gateway and the AWS VPN CloudHub is encrypted.
What is AWS Direct Connect and How is it useful?
AWS Direct Connect is a cloud service solution that makes it easy to establish a dedicated network connection from your premises to AWS.
A dedicated network connection from your data center to AWS.
Private Connectivity — Using AWS Direct Connect, you can establish private connectivity between AWS and your data center or office.
In many cases, you can reduce your network costs, increase bandwidth throughput, and provide a more consistent network experience than internet- based connections.
There are 2 types of Direct Connect connection
- Dedicated Connection — A physical Ethernet connection associated with a single customer. Customers can request a dedicated connection through the AWS Direct connect console, the CLI or the API
- Hosted Connection — A physical Ethernet connection than an AWS Direct connect Partner provisions on behalf of a customer. Customers request a hosted connection by contacting a partner in the AWS Direct Connect Partner Program, who provisions the connection. For Example, Verizon, AT&T etc.,
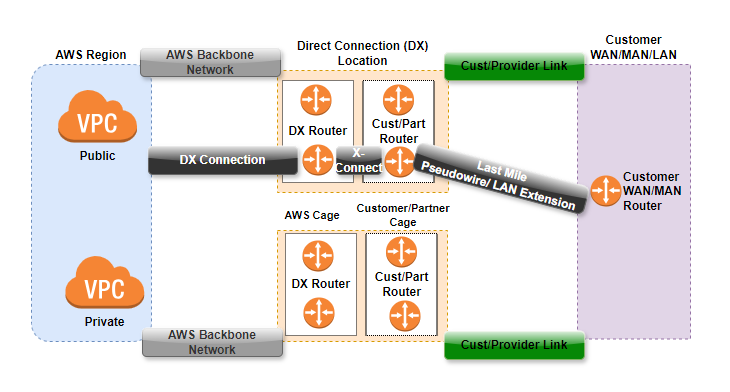
Let us consider VPC Public and VPC Private in the AWS region. We also have Direct Connect Location. They are scattered across all over the world. It is basically the physical location. We also have customer wide area network or LAN.
We have a Cage inside our direct connect connection location. This cage will be owned by AWS and they’ll have their own direct connect router. If we are using AT&T or Verizon, we have the Customer/Partner Cage and have their own routers, where you’ll be using the dedicated option for direct connect. This is own by our own dedicated Cage.
This is routed through Customer router and then we have Customer / Provider link. So this can be MPLS or dedicate line which is connected to the Customer/Partner Cage. We have AWS Backbone Network which connects our VPC to the AWS Cage in that direct connect connection running over the AWS. The DX Connection connects the data center where your VPCs are located to direct connect location.
To run the cross connect, we have X- connect between the AWS Cage and customer/Partner Cage. Finally, we have Last Mile which is LAN extension for the Customer router. This way we establish connection from public or private VPC to the customer network.
VPN Vs Direct Connect
- VPNs allow private communication, but it still traverses the public internet to get the data delivered. While secure, it can be painfully slow.
- Direct Connect is Fast, Secure, Reliable and ale to take massive throughput.
Direct connect can be used —
- We need the direct connection from the data center to AWS.
- Useful for high-throughput workloads ( e.g., lots of network traffic)
- Helpful when you need a stable and reliable secure connection.
AWS Transit Gateway
With all the above networking things, when we expand from single VPC to multiple VPCs and start Peering connection and Direct connect to our data center. The architecture becomes more and more complex which is hard to maintain. This is the problem that Transit Gateway was designed to solve.
AWS Transit Gateway connect VPCs and on-premises networks through a central hub. This simplifies your network and puts an end to complex peering relationships. It acts as a cloud router — each new connection is only made once.
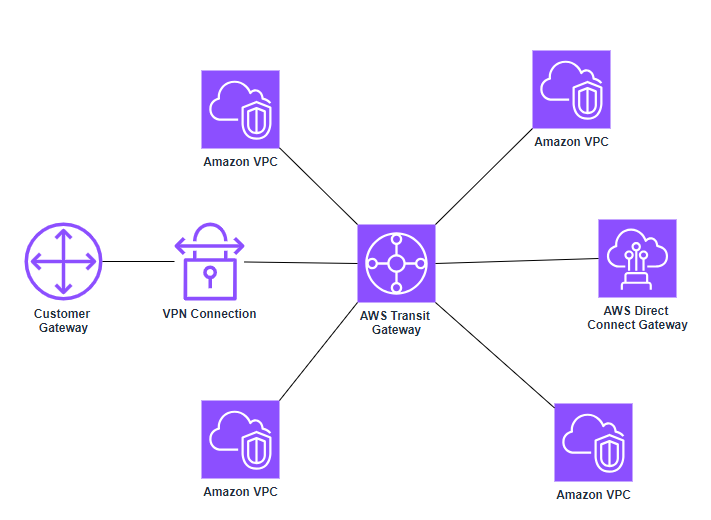
By creating AWS Transit Gateway, we can connect VPCs to Transit Gateway and we only need to do that connection only once and then it’s the same with direct connect in our VPN connections. And then everything that is connected into transit gateway will be able to talk to each other directly. So it’s a way to really simplifying your network topology.
- Allows you to have transitive peering between thousands of VPCs and on-premises data centers
- Works on hub-and-spoke model.
- Works on a regional basis, but you can have it across multiple regions.
- You can use it across multiple AWS accounts using RAM (Resource Access Manager)
- We can use route tables to limit how VPCs talk to one another.
- Works with Direct connect as well as VPN connections
- Supports IP multicast (not supported by any other AWS service) — sending single packet to thousands of hosts across the network like internet mostly used for audio.
5G Networking with AWS Wavelength
What is 5G Networks?
5G provides mobile devices with higher speed, low latency and greater capacity than 4G LTE networks. It is one of the fastest, most robust technologies the world has ever seen.
What does it had to do with AWS Wavelength?
AWS Wavelength embeds AWS compute and storage services within 5G networks, providing mobile edge computing infrastructure for developing, deploying and scaling ultra low latency applications.
For Example, the car sends data to the AWS cloud services and communicate with 5G network where they have AWS device which supports the 5G network and then it communicates back to the car. Also the data from 5G network is also sent to the AWS resources that store this data.
