AWS Series — Best Practices in IAM
In IAM, we have building blocks which are Users, Groups, Roles
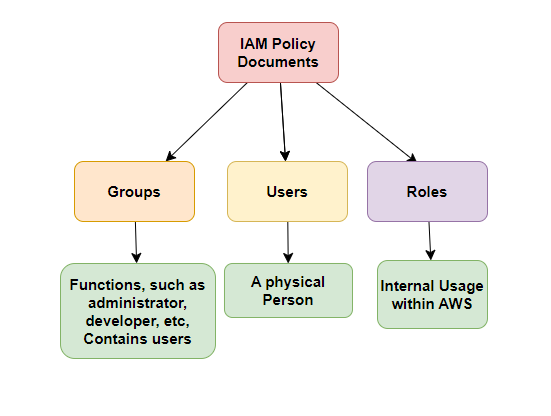
Best practices for Users and Groups
It is always best practice for users to inherit permissions from the groups. When making the changes it can be done at group level.
Always work on the principle that one user one account and the user account should not be shared with multiple people.
Principle of Least Privilege
Only assign a user the minimum amount of privileges they need to do their job.
For Instance, HR team does not need to access virtual machine.
Create an user
Go to IAM and click on Users in the left pane. For creating the user, click on Create User
Now provide the name and we can check the box with Provide user access to the AWS Management Console.
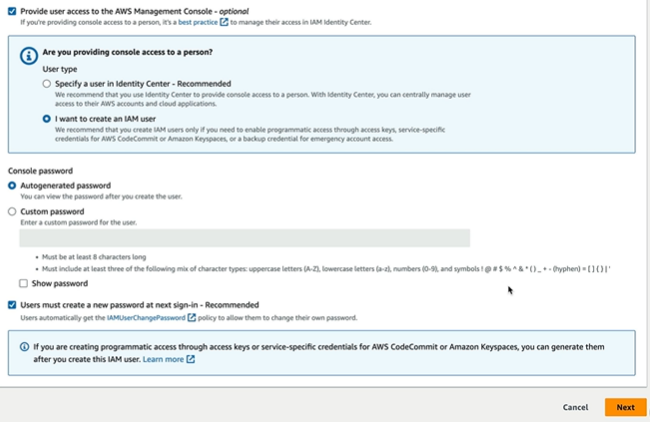
If you are providing access to the console, we should choose if we are going to use Identity Center to maintain the user which is recommended approach. I want to choose create IAM user for this. It would prompt me for Autogenerated/Custom Password and checkbox to choose if user should create new password during next sign in to make it secured.
On clicking next, it will ask to create group or attach policies. But in best practice we said it is always good to have Group with policies attached
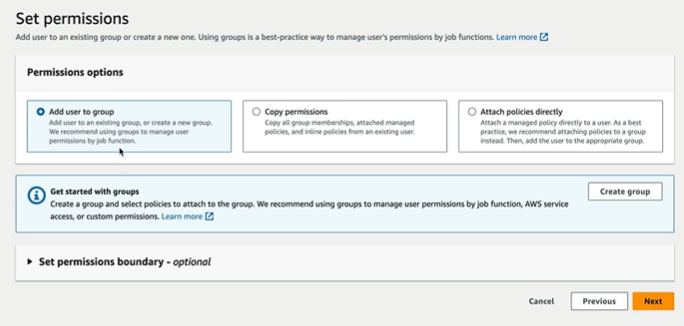
We can create a group here with necessary permissions
Creating Group
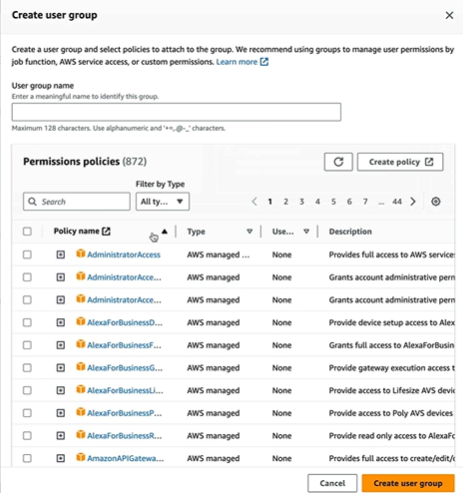
Give the User Group a name and check the policies required for the user. Click on Create user group
On adding user group, it appears here and select it and click on next
We can add Tags with values which helps when we create virtual service and tag it saves lot of time and say the EC2 is owned by Admin Department and the employee with respective ID.
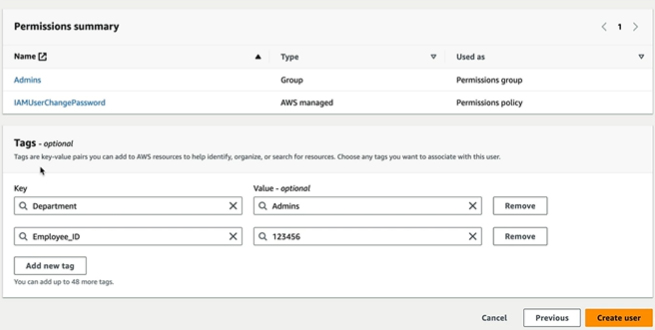
Hit Create user which create user and down the csv file to save the credentials.
There are also some job functions amazon has already populated like Database Administrator, Power User etc.,
Power user has all admin access except they cannot create the user or group.
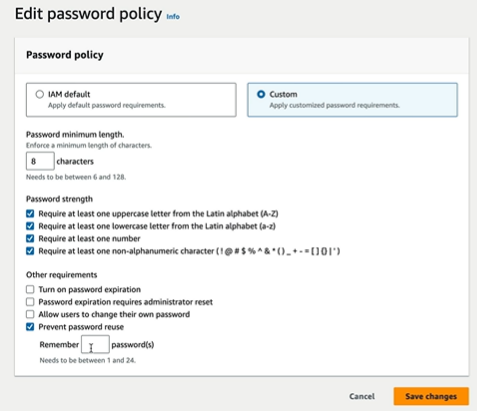
If we look at Account settings, we have password policy
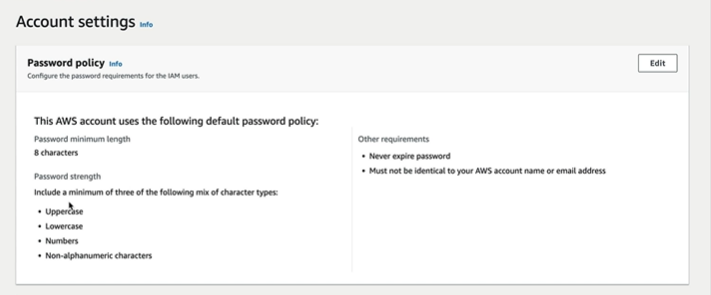
We can also change the policies for the password as per our rules
What if we don’t have any group assigned to the user while creating them? Their permissions look like this
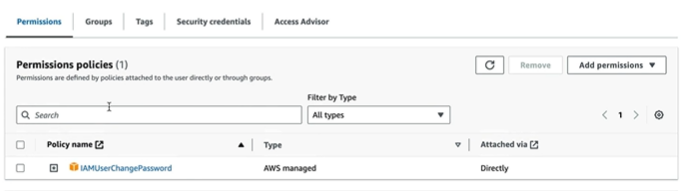
It just has IAM User change password and does not have access to any resources. So it is important to add groups or policies to the user while creating them. To have programatic access, we can click on access Key

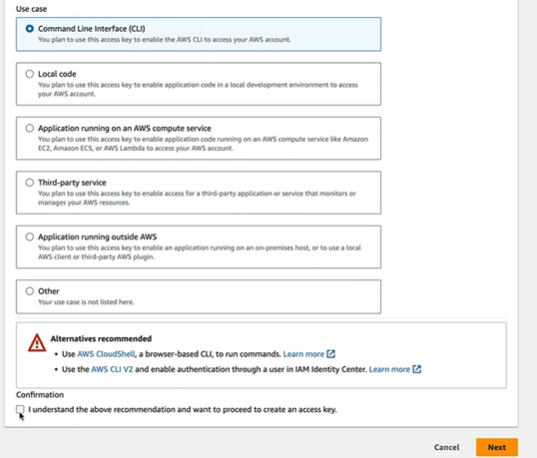
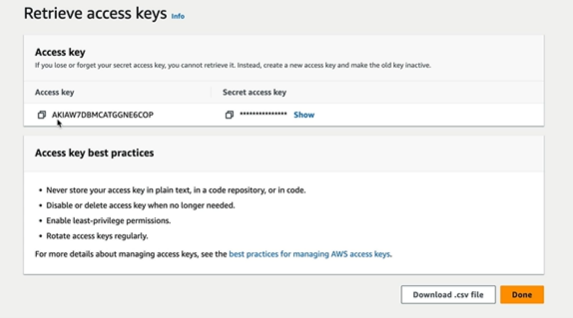
It is going to create Access key and access key ID. Once we choose the use case and click next we get the access keys
Identity Providers allow us to connect IAM to Active Directory in Corporate Network.
There are 2 types of providers that are supported. SAML and OpenID Connect
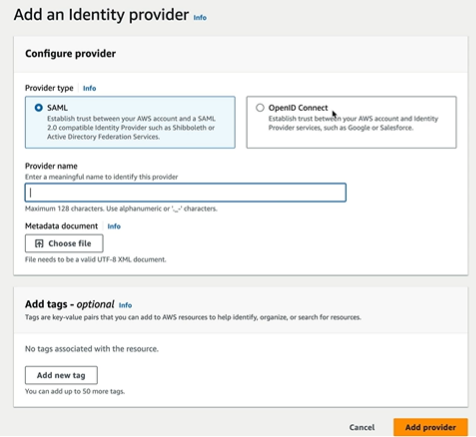
SAML which is Active Directory Federation Services and OpenID Connect supports Google, Salesforce etc.,
Summary
- IAM is universal — It does not apply to regions at this time.
- The Root Account — The Account created when you first set up your AWS account and which has complete admin access. Secure it as soon as possible and do not use it to log in day to day.
- New Users — No permissions when first created.
- Access Key ID and secret access keys are not the same as usernames and passwords.
- You only get to view these once — If you lose them, you have to regenerate them.
- Always set up password rotation — You can create and customize your own password rotation policies.
- IAM Federation — you can combine your existing user account with AWS. For example, when you log on to your PC(Usually using Microsoft Active Directory), you can use the same credentials to log in to AWS if you set up federation.
- Identity Federation — Uses the SAML standard, which is Active directory.
