AWS Series — Why IAM roles are important for interacting between resources
AWS Identity and Access Management (IAM) is a service that allows AWS customers to manage user access and permissions for their accounts, as well as available APIs/services within AWS. IAM can manage users and security credentials (such as API access keys), and allow users to access AWS resources. In this lab, we will walk through the foundations of IAM. We’ll focus on user and group management, as well as how to assign access to specific resources using IAM-managed policies. We’ll learn how to find the login URL, where AWS users can log in to their account, and explore this from a real-world use case perspective
What is an IAM Role?
A role is an identity you can create in IAM that has specific permissions.
A role is similar to a user, as it is an AWS identity with permission policies that determine what the identity can and cannot do in AWS.
It uses JSON and policy documents. However, instead of being uniquely associated with one person, a role is intended to be assumable by anyone who needs it.
Roles are Temporary. A role does not have standard long-term credentials the same way passwords or access keys do. Instead, when you assume a role, it provides you with temporary security credentials, for your role session.
What else can Roles do?
Roles can be assumed by people, AWS architecture, or other system-level accounts.
Roles can allow cross-account access. This allows one AWS account the ability to interact with resources in other AWS accounts.
To understand better, Let us create one IAM role and provide S3 access and Attach the role to EC2 instance. Try to access S3 from EC2.
Go to IAM > Roles > Create Role.
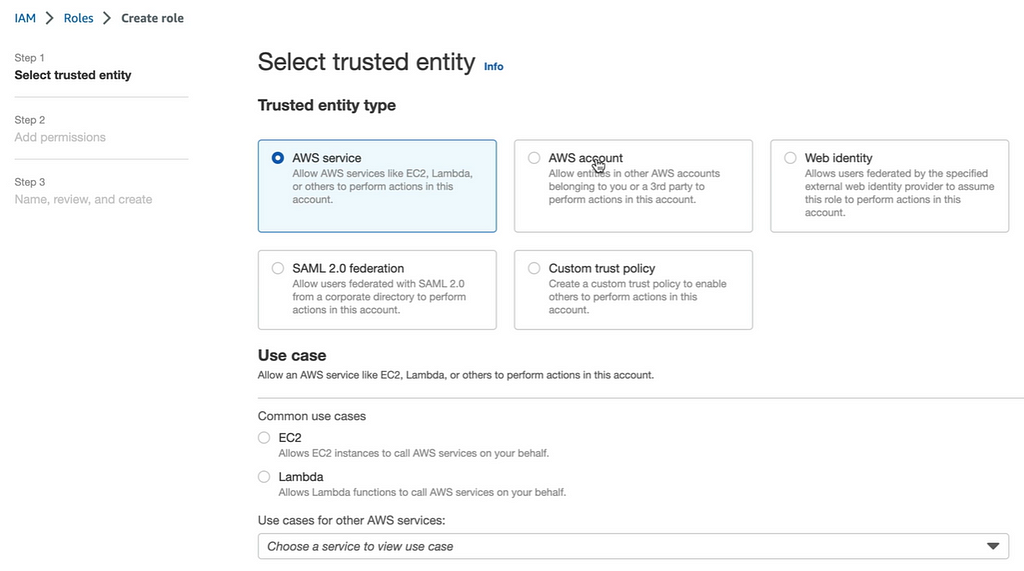
Select AWS service and select EC2. On typing next, we have to select the permission policies. We are going to select AmazonS3FullAccess.
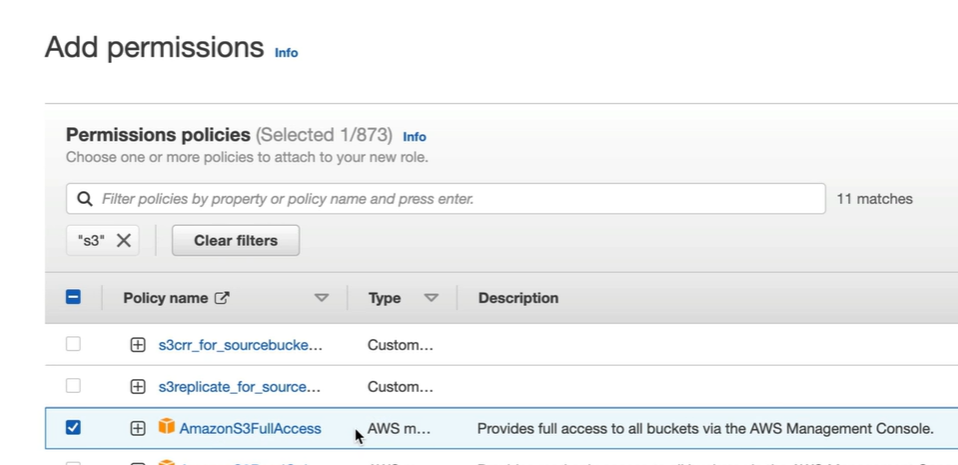
Click on Next and give the Name of the role and you can also see the JSON with the permissions.
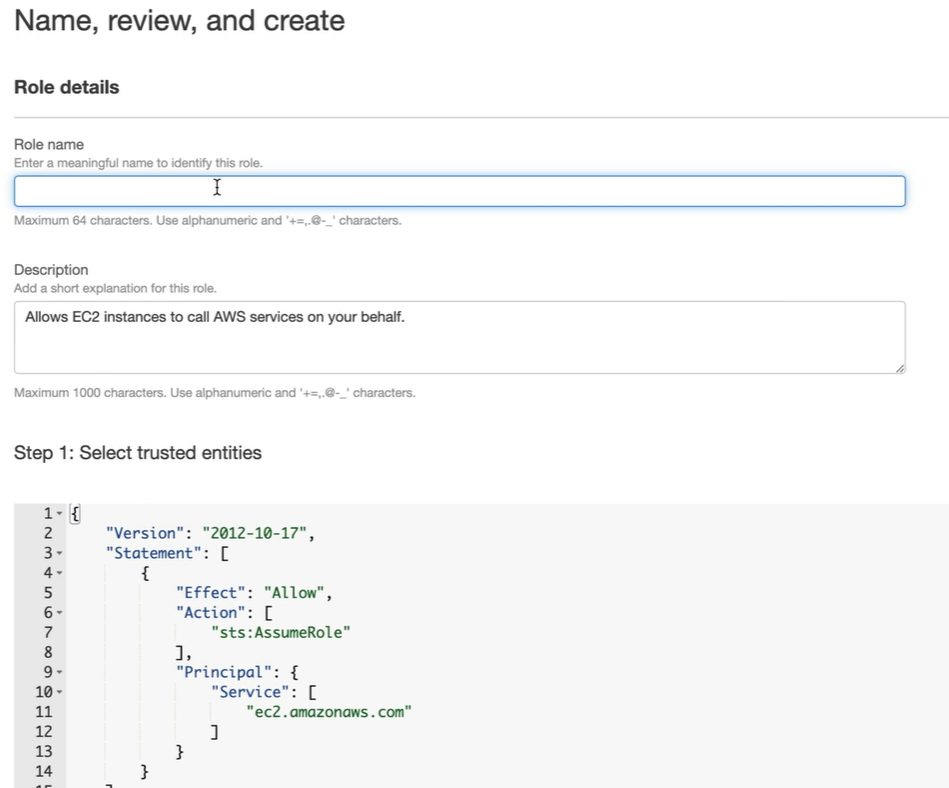
Create the Role. This creates roles with S3 admin access from EC2.
Create a basic EC2 instance
AWS Series — EC2: An AWS Virtual Machine
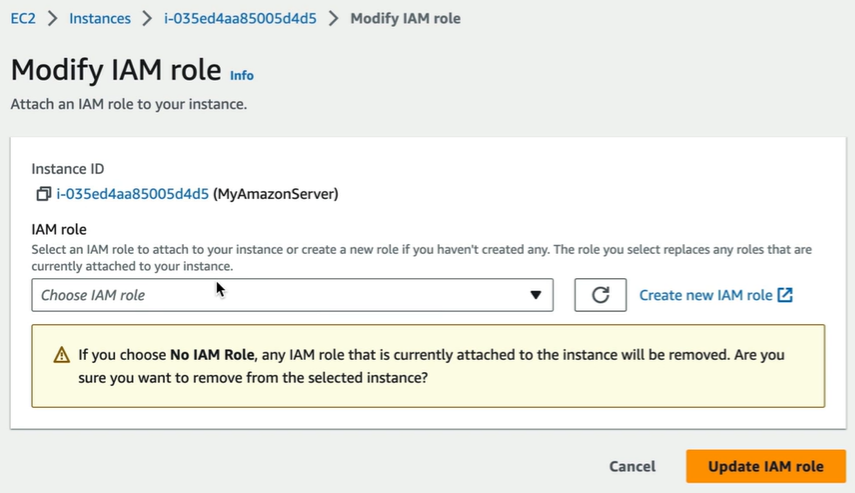
Now select the instance > Go to Actions > Security > Modify IAM Role.
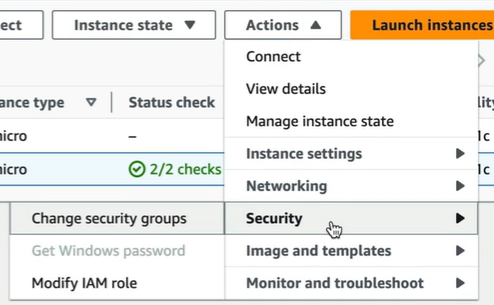
Select the role that we created with S3 Admin access and click on Update IAM role.
Now Go to EC2 Instance and connect. Provide the command for s3 “aws s3 ls” to list all the buckets in my S3 account. We will be able to generate the list which means we have access to s3 account.
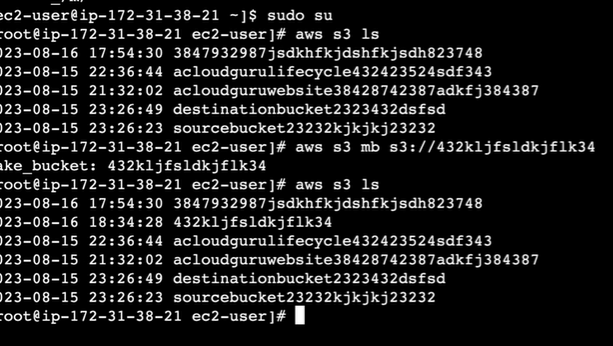
The IAM role is most secured way of connecting resources. In this case, it is EC2 to S3. This way the access key will not be leaked and the only way to access S3 would be logging in to the EC2 server.
The moment we terminate this EC2 we loose access to S3 server.
Points to remember while using IAM Roles —
- The Preferred option from a security perspective
- Avoids Hard-coding of credentials — It provides access without use of access key IDs and secret access keys.
- Policies control the role’s permissions.
- You can update a policy attached to a role, and it will take immediate effect.
- You can attach and detach roles to running EC2 instances without having to stop or terminate those instances.
