Microservice Architect Series — Do you know what Service discovery Do?
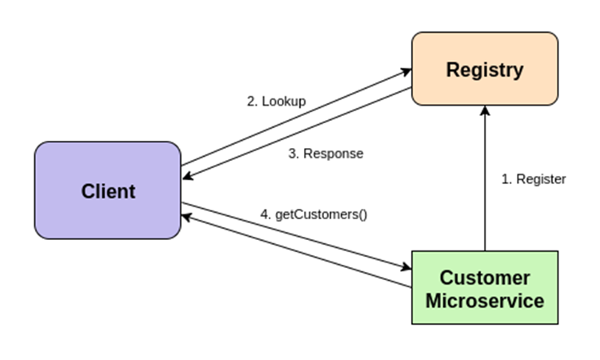
In a microservices architecture, service discovery is a critical component that allows services to find and communicate with each other without hardcoding network locations. Effective service discovery ensures that microservices can scale, are resilient to failures, and can be easily managed and monitored. Here are some of the best ways to implement service discovery, covering both client-side and server-side discovery mechanisms.
1. Client-Side Discovery
In client-side discovery, the client is responsible for determining the locations of available service instances and balancing the load among them.
Using Service Registries —
A service registry is a database of available service instances. Clients query the service registry to get the addresses of service instances. Some popular service registry tools include:
- Eureka: Developed by Netflix, Eureka is a popular choice for client-side discovery in the Spring Cloud ecosystem.
- Consul: A versatile service registry that also provides features like health checking, key-value storage, and multi-data center support.
- Zookeeper: Originally developed for Hadoop, Zookeeper is a distributed coordination service that can be used for service discovery.
How It Works —
- Service Registration: Each service instance registers itself with the service registry upon startup and deregisters upon shutdown.
- Service Lookup: Clients query the service registry to discover service instances, typically using a library provided by the registry tool.
- Load Balancing: Clients implement load balancing strategies (e.g., round-robin, random, weighted) to distribute requests among available instances.
Example Workflow —
- A client needing to call the “Order Service” queries the service registry.
- The registry responds with a list of available “Order Service” instances.
- The client selects an instance based on its load balancing strategy and makes the request.
2. Server-Side Discovery
In server-side discovery, a load balancer or proxy sits between the client and the service instances. The client makes a request to the load balancer, which then determines the service instance to handle the request.
Using Service Registries with Load Balancers —
The service registry is still used, but the load balancer queries the registry instead of the client. Popular load balancers for server-side discovery include:
- AWS Elastic Load Balancing (ELB): Integrates with AWS services to provide dynamic load balancing.
- NGINX: Can be configured with a service registry like Consul to dynamically update its upstream server list.
- HAProxy: Another robust load balancer that can integrate with service registries.
How It Works —
- Service Registration: Service instances register with the service registry as in client-side discovery.
- Service Lookup: The load balancer queries the service registry for available service instances.
- Request Routing: The load balancer routes incoming client requests to appropriate service instances based on the current list.
Example Workflow —
- A client makes a request to the “Order Service” through the load balancer.
- The load balancer queries the service registry for available “Order Service” instances.
- The load balancer selects an instance based on its algorithm and forwards the client’s request to that instance.
3. Service Mesh
A service mesh provides advanced service discovery along with other features like traffic management, security, and observability. It typically involves a control plane and data plane architecture.
Popular Service Meshes —
- Istio: A comprehensive service mesh that works with Kubernetes and other platforms.
- Linkerd: A lightweight service mesh designed for simplicity and performance.
- Consul Connect: Extends Consul with service mesh capabilities.
How It Works —
- Sidecar Proxies: Each service instance runs a sidecar proxy (e.g., Envoy) that handles communication with other services.
- Control Plane: Manages configuration and policies, distributing them to sidecar proxies.
- Service Discovery: The control plane interacts with the service registry to maintain an updated view of available services.
Example Workflow —
- A client makes a request to the “Order Service” through its sidecar proxy.
- The sidecar proxy consults the control plane for the best instance of the “Order Service.”
- The sidecar proxy forwards the request to the selected instance, ensuring consistent policies and observability.
Best Practices for Service Discovery
1. Health Checks: Ensure that your service registry supports health checks to verify that service instances are alive and healthy before routing requests to them.
2. Consistent Configuration: Maintain consistent configurations across service instances and discovery tools. Use tools like HashiCorp Consul or Spring Cloud Config to manage configurations centrally.
3. Scalability and Performance: Choose service discovery tools and architectures that can scale with your application. Performance is critical, so prefer tools that offer low-latency lookups and efficient load balancing.
4. Security: Implement security measures to protect service discovery mechanisms. Use mutual TLS for secure communication and ensure that only authorized services can register and query the registry.
5. Monitoring and Observability: Integrate monitoring and logging solutions to gain visibility into the service discovery process. Tools like Prometheus, Grafana, and ELK Stack can help track metrics and logs.
Conclusion
Service discovery is a foundational component of microservices architecture, enabling dynamic service location and communication. By carefully choosing the right approach — whether client-side discovery, server-side discovery, or service mesh — and following best practices, you can ensure robust and efficient service discovery in your microservices environment. As with any architectural decision, consider your specific use case, scalability requirements, and operational complexity to select the best solution for your needs.
